Update June 16, 2025
It turns out that this blog was kind of pointless… Fellow Swiss MVP Andres Bohren pointed out that the MSIdentityTools PowerShell module can already get a company display name and the default domain of a tenant by Id. A quick look at MSIdentityTools.psm1 revealed that it’s possible to resolve a tenant name/domain by Id without even installing the module.
Required Permissions
You’ll need the CrossTenantInformation.ReadBasic.All permission to perform these requests. The permission supports both delegated and application authentication.
Resolve Default Domain and Name by Tenant Id
|
|
Find Tenant Id by Domain
|
|
You can query any domain verified in a tenant to get its Id. It doesn’t need to be the tenant’s default domain. I think this could actually be a bit problematic in some cases as it could potentially reveal more information that you might intend to at a given time.
For example, I’m thinking about a scenario where a company is about to launch a new product or acquire another company and thus has already set up a specific domain in their tenant for said event, but the information isn’t public yet.
Anyway, thanks for this great tip Andres!
Original Article
If you work a lot with Microsoft Entra ID a lot, you probably already know the Tenant Lookup Website created by the Microsoft 365 U.S. Government Programs team. However, the lookups this website performs only work in one direction. You can only get a tenant id, if you already know one of its connected domains but you can’t get a tenant’s domain or name just off of a tenant id.
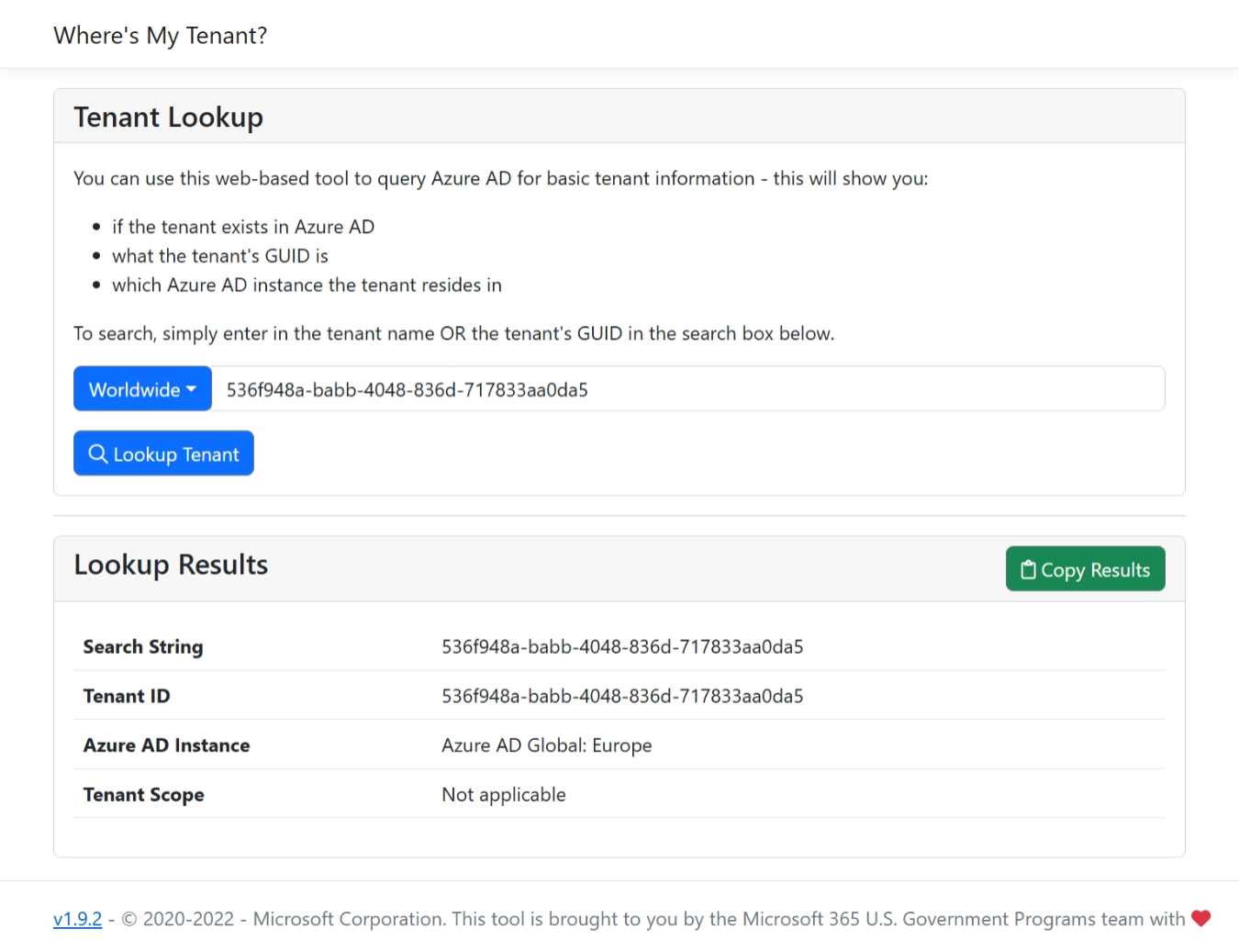
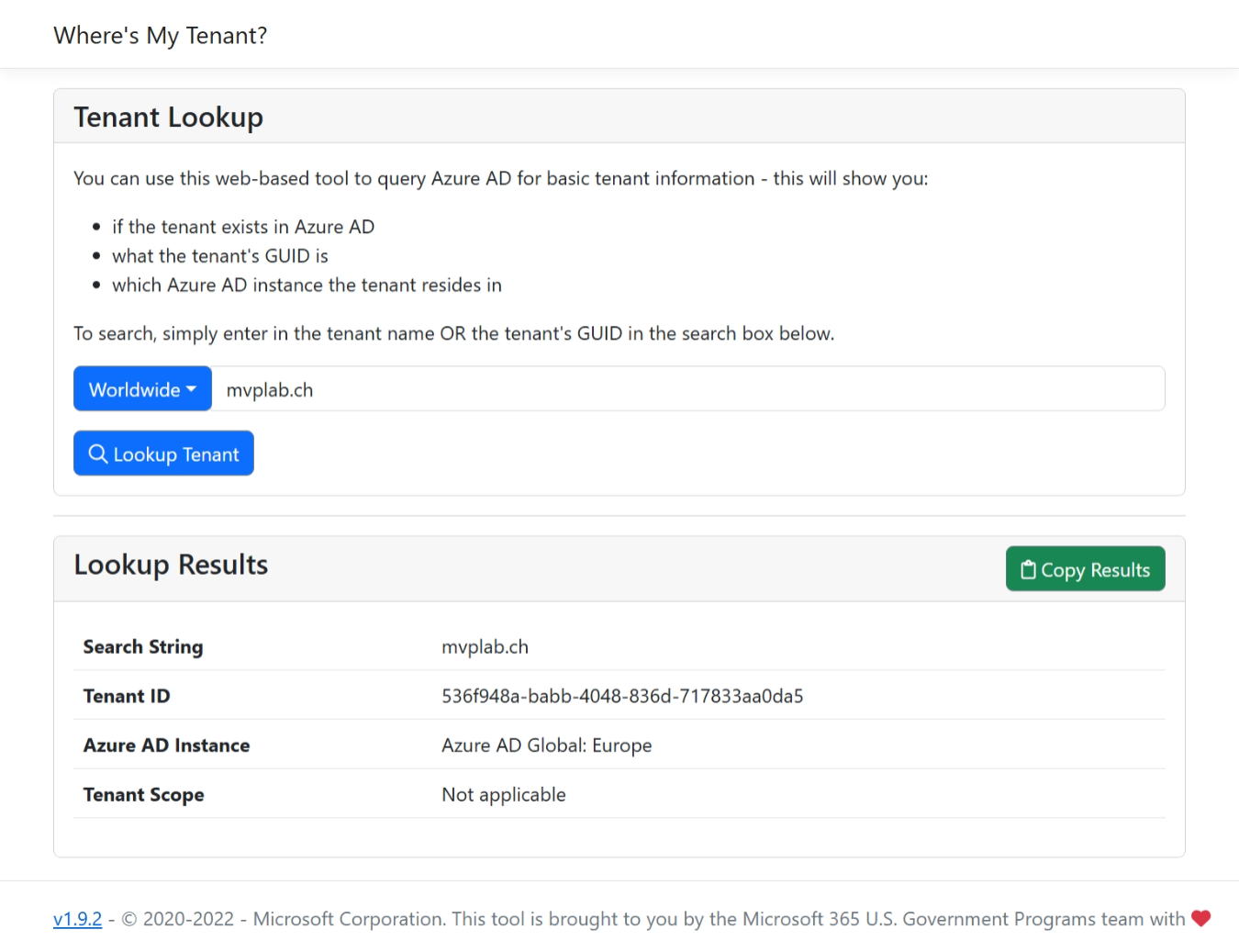
I’m not sure how well known this technique is but when I was still working as a consultant for lots of different companies, I also worked in a lot of different tenants. So, I used this trick quite often. You can actually sign into a specific tenant by appending /<tenant id> to i.e. https://portal.azure.com.
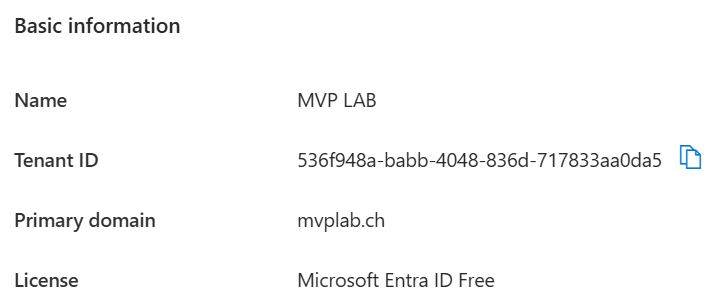
So, to access my MVP LAB tenant directly, I can just go to https://portal.azure.com/536f948a-babb-4048-836d-717833aa0da5 or even https://portal.azure.com/mvplab.ch.
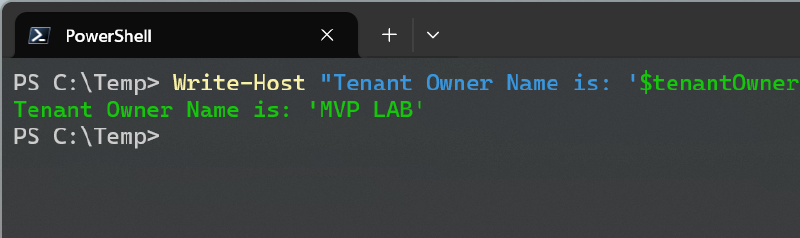
This will open my tenant’s sign in page. If no company branding is applied, it doesn’t tell you much. However, if you view the page source and search for sCompanyDisplayName it will tell you the name of the tenant.
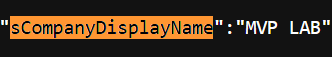
The company display name is the one you see in Entra ID’s Overview.
If a company is using custom branding, it’s even more straight forward to learn more about a tenant’s owner. For example, this is LinkedIn’s sign-in page.

The page source doesn’t expose any domains or other unique values. You can only see the company display name or if the tenant has custom branding, you may be able to tell who the tenant belongs to by looking at their logo or background. However, in most cases, this is already better than just knowing a tenant’s id.
Remeber to always be vigilant and that bad actors might create fake tenants which try to trick you into thinking that they’re a legit organization by using another companies branding.
Doing it Programmatically with PowerShell
You can also get the company display names programmatically with the PowerShell code below.
|
|
Use Cases
Check App Owner Tenant Id of Multi Tenant Apps in your Tenant
Why would you want to do this? Let’s stick with the example of LinkedIn. You might have wondered how I was even able to get a hold of LinkedIn’s tenant id? Well, I have added LinkedIn as an Enterprise Application to my tenant. When I check out the service principal of the Linked in app under Enterprise Applications in Entra ID, it only shows the Homepage URL but no tenant id.
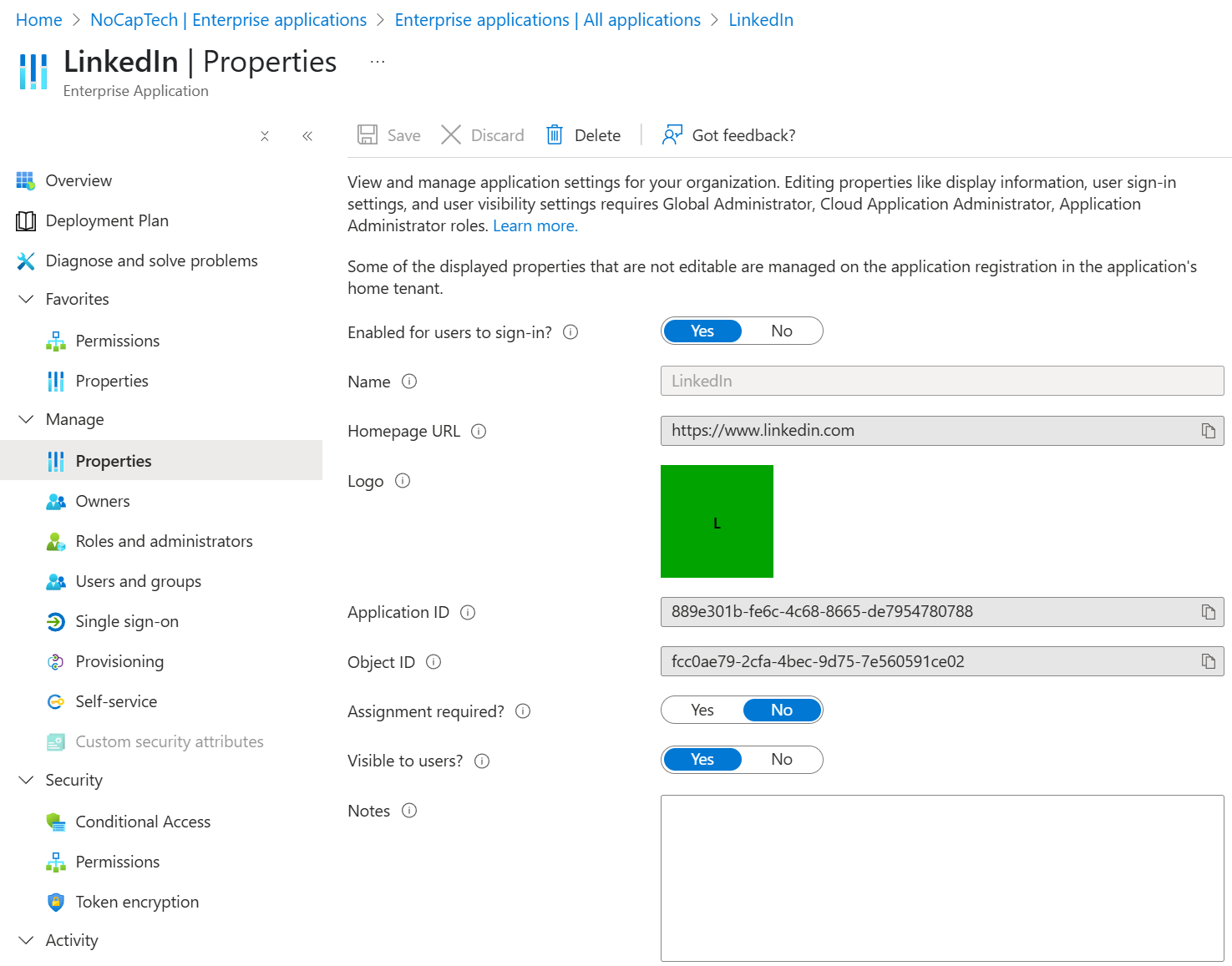
This app is registered as a multi tenant app in LinkedIn’s tenant. When I granted consent to it, a service principal for the app got created in my tenant. To get the tenant id of the tenant where it’s registered, I can run Get-MgServicePrincipal with the service principal’s object id. (The service principal object id is unique in every tenant where the app was added.)
|
|
The Entra Portal doesn’t surface this information but Graph does. That’s how I was able to get to LinkedIn’s sign in page.
Apps that allow sign in with a personal Microsoft Account will list 9188040d-6c67-4c5b-b112-36a304b66dad as AppOwnerOrganizationId. You can find more information here.
Check Sign-In Logs of Users
Another good use case is when you’re reviewing sign-in logs. If some of your users are guests in other tenants, the sign-in logs will only reference a tenant id but not a tenant name or domain. So, you won’t actually know the names of the tenants to which they sign in.
To create some sign-in logs for testing and demonstrating this, I opened https://myaccount.microsoft.com/mvplab.ch and signed in with the identity of a user which is a guest in this tenant. Note that with https://myaccount.microsoft.com it will only work if you append /<domain>. Appending /<tenant id> won’t work. But when you sign in with /<domain>, you’re directly taken to that organization and not your own.
If I check the audit log in the user’s home tenant now, I can see that there was a guest login in a different tenant. The tenant where the sign-in happened is called Resource tenant.
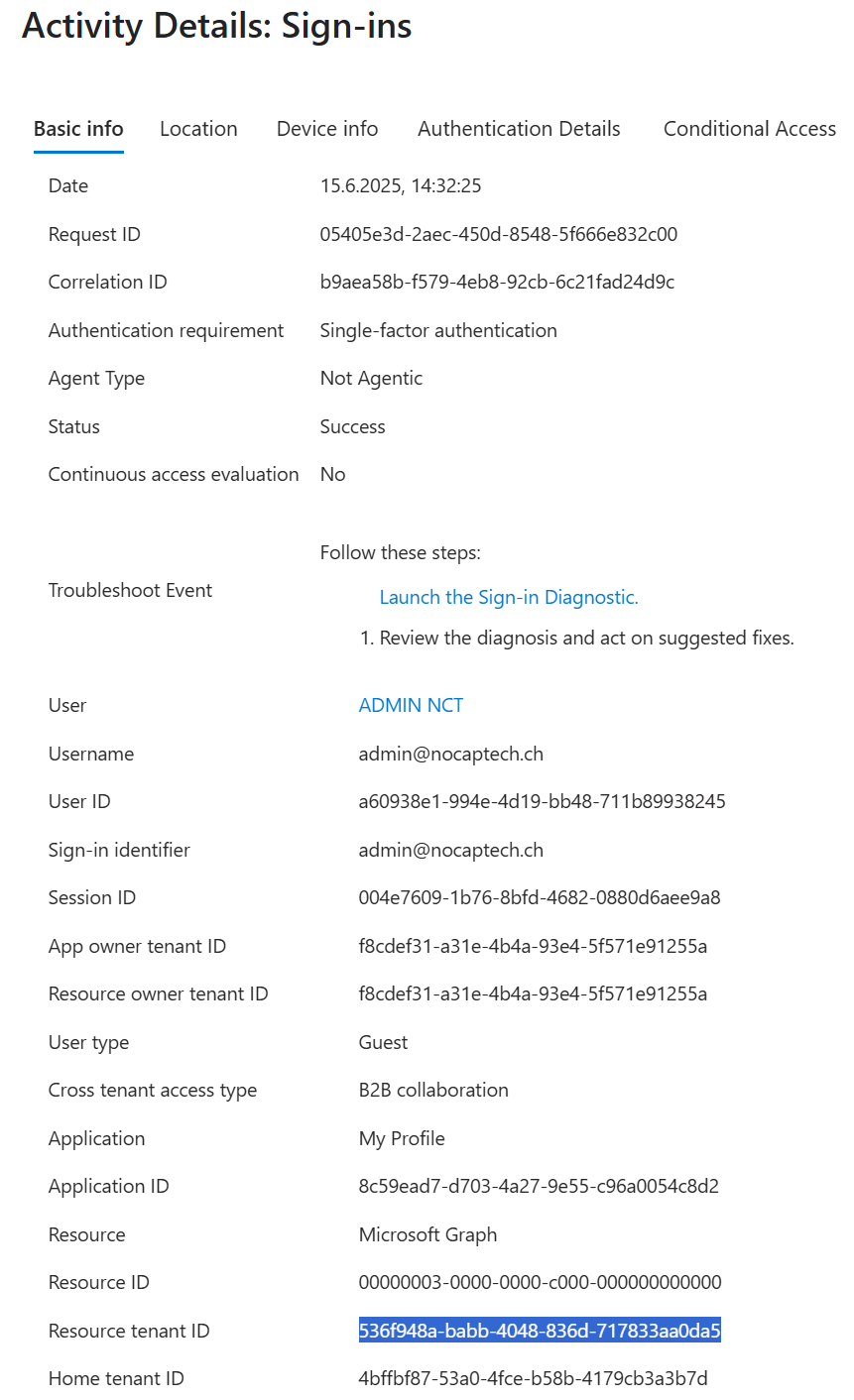
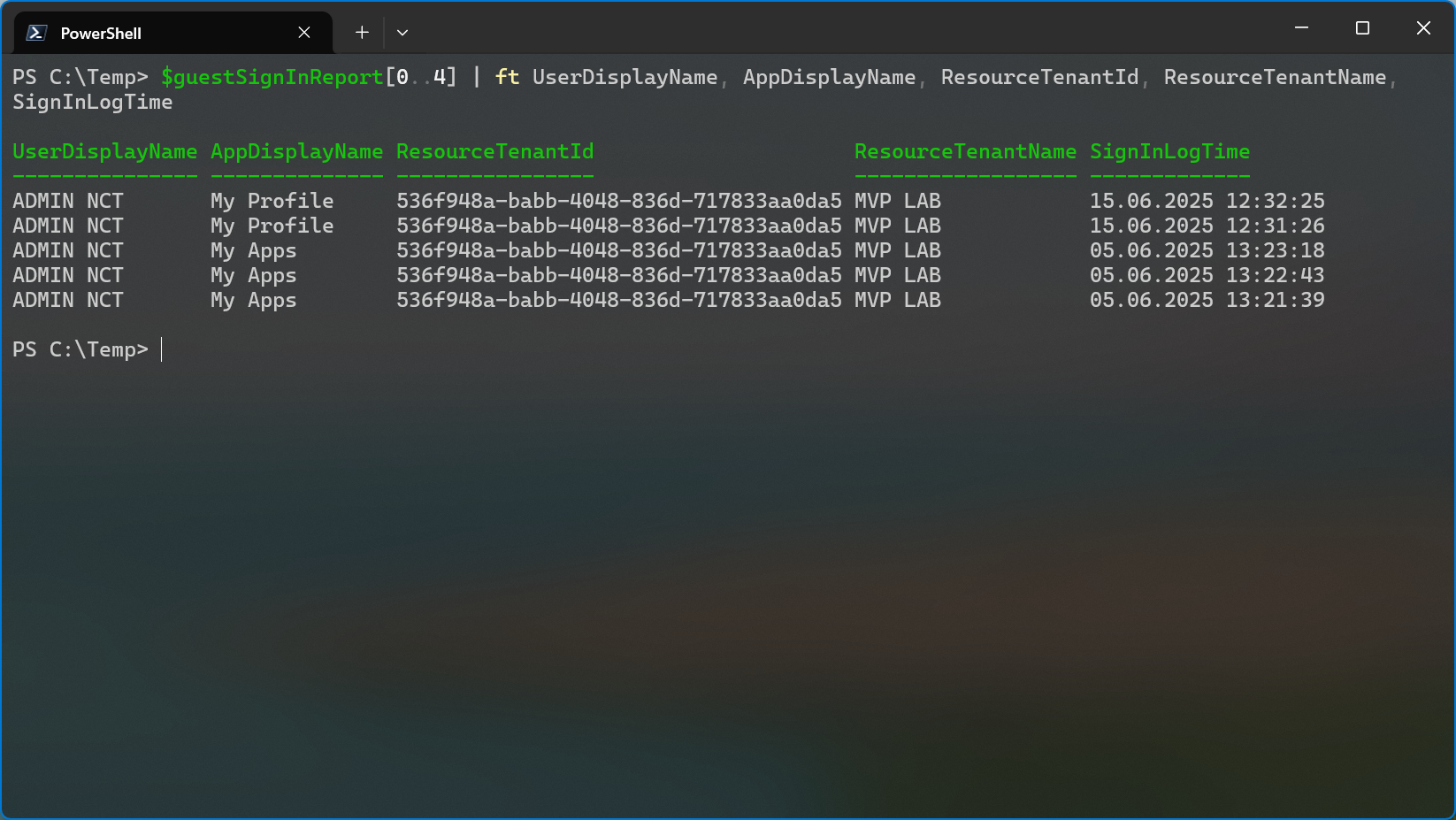
Filter Sign-In Logs for Guest Sign-Ins and Get Tenant Name
Since I already provided a way of programatically finding tenant names above, all I needed to create a report which lists guest sign-ins including the resource tenant’s display name, was to to retrieve the sign in logs through the Graph API.
Only the Beta api returned the userType property. Funny enough, the Entra ID portal is using the Beta API as well…
|
|
Requests to the sign-in page are only made once per unique tenant id. Unfortunately, I didn’t have a third lab tenant handy so I can’t really show different tenant names in the output but you get the idea.
Summary
I hope that this blog post helps you to make your life a little easier since you now know that you can qucikly sign into a different tenant by appending the tenant id or tenand domain to the Azure Portal URL. I also hope that the technique to find tenant names when all you have available is a tenant id outlined in this article is helpful to you so you can get a better understanding of which tenants your users sign in to as guests.